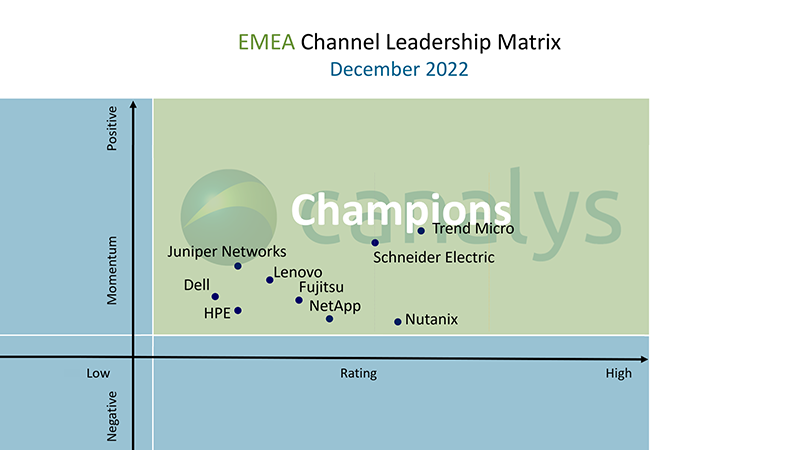
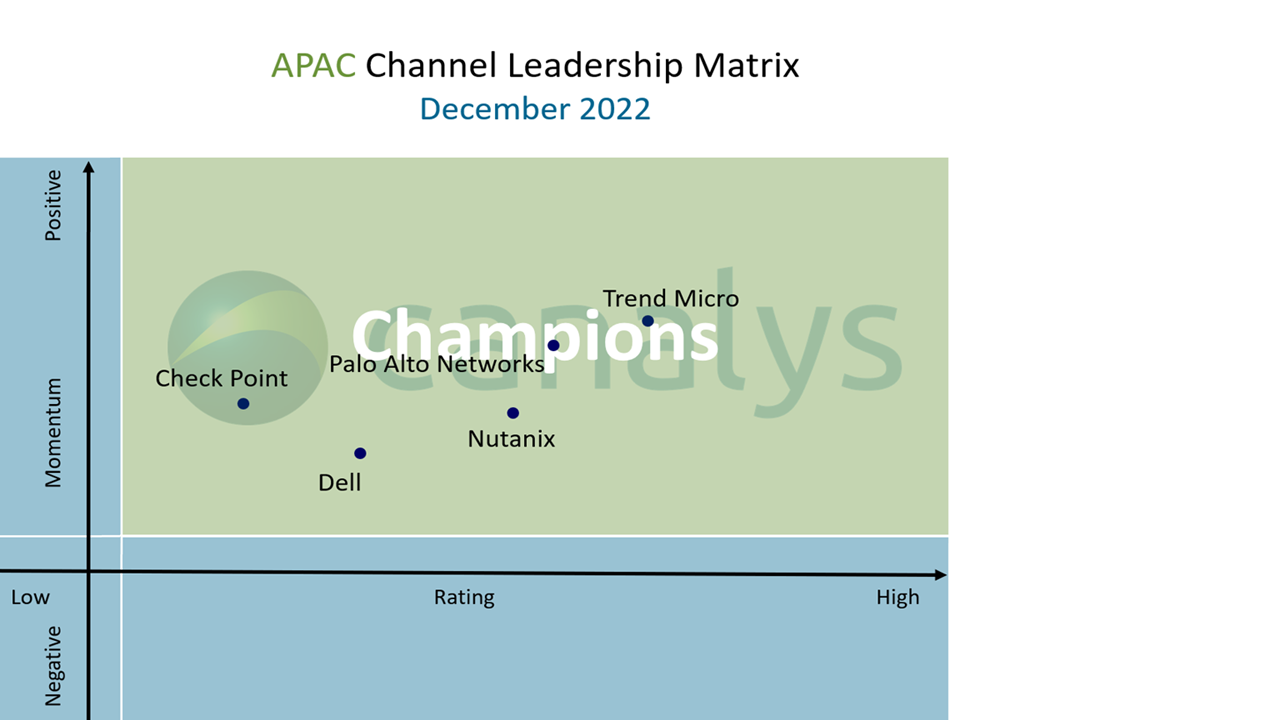
BYOD rises in popularity
BYOD is not going away, as highlighted in the latest Canalys Consumer Insights Survey from November 2022 with 5,000 consumers in France, Germany, Italy, Spain and the UK.
Since the pandemic, the shift to remote and hybrid working has cemented the BYOD (bring your own device) trend in businesses in the advanced economies of Europe. As BYOD increases, mobile device security has become more important, particularly for smartphones, where device security and mobile device management (MDM) issues have become critical. This has forced many companies to standardize on a few select vendors for their authorized BYOD-approved devices as IT departments contend with increased threats and attacks on their corporate networks.
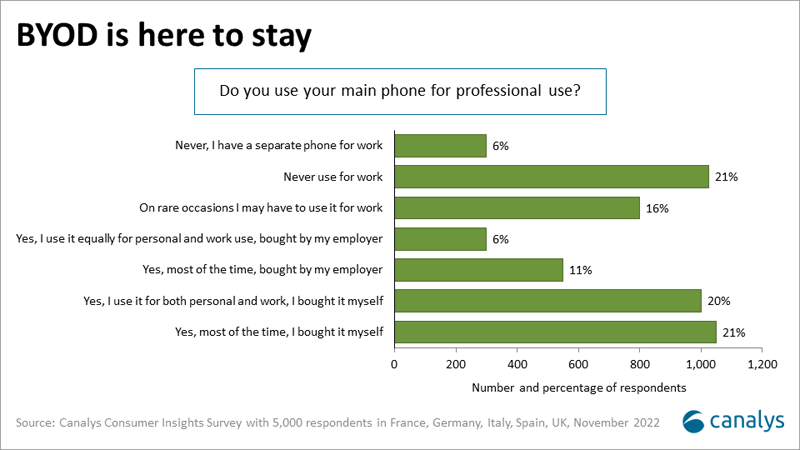
BYOD is not going away, so supporting it has become a necessity for most businesses, as highlighted in the latest Canalys Consumer Insights Survey from November 2022. 41% of 5,000 respondents in Western Europe use their personally bought smartphones for both professional and personal use. In addition, the data suggests some employers already have a remote working device strategy, as 17% of respondents are provided with smartphones that they can also use on a personal basis.
As BYOD grows, so do security and privacy issues
BYOD and remote working were not new to most IT departments. Still, the pandemic accelerated the need for remote working and forced IT departments to formalize device management and BYOD programs. But the legal, privacy and security requirements of supporting a hybrid device environment have created an opportunity for the channel to advise on approved vendors for device management software, smartphones, PCs, laptops and other mobile devices.
BYOD is attractive to employees, but many companies underestimate the investment needed to ensure all have suitable devices that are secure and comply with data privacy legislation. The MDM costs that come with authorized access, secure data usage, device repairs and any network downtime can be substantial. Companies must also provide security software on each device to prevent confidential information from leaking, and that can be a significant cost, even for a smaller business. Despite the increased investment in security infrastructure due to the threat of security breaches, companies recognize that BYOD does have benefits:
- Employees get their choice of the latest device, and there may be a small saving for the employer if the employee pays for the device.
- At the most basic level, BYOD improves productivity by allowing employees access to work emails from their devices. For example, clearing one’s inbox while on public transport or during downtime at home can be satisfying and allow more flexibility in the workday, as well as allowing office or home working to increase employee satisfaction.
- BYOD results in increased personal productivity as people prefer to use their own devices and are often more effective on their own smartphones or personal PCs if the models are newer than those provided at work. Emails might build up during the day and can be cleared or at least read away from the workplace. Reading news relevant to one’s job, watching a training video or a replay of a presentation can also easily be done. In addition, it is convenient for employees not to have to carry and manage two devices between the office and home if they are working flexibly.
BYOD will continue to challenge the wider mobile device ecosystem
Flexible remote working has put IT departments under pressure to maintain corporate data security while allowing employees to use various devices with maximum functionality. This has created opportunities for the mobile B2B channel and affected multiple players in the ecosystem:
- The B2B channel must provide mobile security and MDM software solutions and enable companies to set policies to limit work activities for BYOD. It is common for employees to carry out unapproved tasks on their BYOD products, which is an area prime for conflict, so rules are imperative. Privacy also works both ways – it is as much of a concern to an employee who does not want to use a company-issued smartphone for personal use because they wish to keep their personal contacts and contents private, as it is for an employer who wishes employees keep personal information separate from their work device.
- Demand for channel expertise and sales of vetted mobile devices has increased. The selection of mobile device brands compatible with security software with wipe/erase functionality to protect data is important to businesses. This list may be restricted to a few select vendors that comply with particular security and network interoperability requirements. Employees will have a limited choice of devices that meet qualifying criteria set by IT departments and IT channel partners.
- The telco channel has had to evolve its sales approach and become less reliant on vendors with a direct sales force to drive B2B sales as BYOD grows. Most large telcos have had to develop multivendor MDM and mobile device security skill sets as customers increasingly demand their consultative sales advice when selling and implementing these solutions. Also, telcos must provide robust, mission-critical MDM solutions that they, or a third-party provider, support. Additionally, the BYOD trend has also resulted in additional margin pressure on business accounts as some of that revenue is transitioning to less lucrative personal contracts instead.
- For smartphone vendors selling directly to businesses, there is pressure to create dual-purpose devices that appeal to the consumer but satisfy IT departments’ needs and qualify them onto “approved lists”.
- Consumer devices such as iPhones and iPads dominate, and even though Android devices are gaining share, there are plenty more opportunities for OEMs to tailor their B2B marketing efforts to enterprises with specific devices (such as ruggedized smartphones for manufacturing or construction) and to verticals (such as financial services or healthcare). These verticals are more likely to impose stricter policies regarding which devices can be used to access corporate data and applications.
- Developers must address the added restrictions imposed by IT departments at the user level, making sure their applications are compliant with MDM software, security policies on data access and communication, and/or that they can run separately as an “isolated” app on the device. On the business application side, flexibility will be important. Applications must run on different versions of smartphone operating systems, regardless of which brand or device age they have. In addition, if these software upgrades are to be done automatically and centrally rather than over the air directly on devices and managed by IT, these will need an additional level of security and/or be managed and given access rights at a corporate network level that has even more complex security requirements. Mobile enterprise applications need to run on a single platform. It must also extend to licensing agreements, as traditional models of employer licensing and software distribution will need to evolve.
Further challenges for vendors, the channel and IT departments will come as “as a service” offerings expand. Such offerings are becoming more common with the implementation of recent programs, such as Microsoft’s “Windows-as-a-Service” offering and Windows 365 Boot, Amazon WorkSpaces, and revamped Citrix Windows and virtualization programs – all aimed at BYOD or shared devices. As the concept of BYOD broadens to include software and services, and as employees use cloud services and other tools on the web, B2B mobile opportunities will become even more plentiful – yet challenging – for all players involved.
Share this article
CATEGORY
- All
- Canalys Forums
- Canalys Forums,Channels
- Canalys Forums,Channels,Partner Program
- Canalys Forums,Channels,Sustainability
- Canalys Forums,Sustainability
- Enterprise
- Market
- Market,Canalys Forums,Channels
- Market,Canalys Forums,Channels,Cloud
- Market,Canalys Forums,Channels,Sustainability
- Market,Channels,PC
- Market,PC
- Market,Smartphone
- Market,Technology,AR/XR/VR
- Market,Technology,Automotive
- Market,Technology,Canalys Forums,Channels
- Market,Technology,Canalys Forums,Channels,Cloud
- Market,Technology,Channels
- Market,Technology,Channels,Cloud,Partner Program
- Market,Technology,Smart Personal Audio
- Market,Technology,Smart Speaker
- Market,Technology,Smartphone
- Smart Personal Audio
- Smartphone
- Technology
- Technology,Canalys Forums,Channels,Security
- Technology,Channels
- Technology,Channels,Cloud,Partner Program
- Technology,Channels,Partner Program
- Technology,Unified Communications
- Technology,Wearable Band