
Canalys Forums 2022 Expert Hubs: Into the breach
A summary of the main talking points from our expert panel discussing how channel partners can minimize the impact of cyber-attacks on their customers.
Canalys ran a series of “Expert Hubs” at its APAC and EMEA Canalys Forums in 2022. The aim was to gather experts within the channel partner community to discuss a variety of subjects. In this series of Canalys Forums 2022 blogs, we summarize some of the key points. This article is from the “Into the breach” cybersecurity sessions.
Participants
APAC: eSentire, Exclusive Networks, Galaxy Office Automation, Interlinked, SecureWare, Tecala, Virtual Graffiti
EMEA: Advania, eSentire, Ivellio-Vellin k2 IT, Matrix IT, N-able, Softcat, Warpcom
Key points
Cybersecurity must be a priority for every organization, but the reality is that not all take it seriously until they are breached. It is no longer just governments and large enterprises that are targeted by ransomware gangs and nation states, but also SMBs, which remain largely unprepared and ill-equipped. This is creating opportunities for channel partners to play a vital role in increasing their customers’ cyber-resilience via managed services. But this involves more than building additional layers of defenses and monitoring activity. Assessing risk and determining accountability, as part of comprehensive incident response plans, are critical elements partners need to establish.
Threats have escalated, but customers are starting to be more proactive
Unsurprisingly, the overwhelming consensus among the panelists in both regions was that the threats faced by their customers have escalated over the last 12 months. The commoditization of ransomware-as-a-service and the increasing sophistication of social engineering techniques used by threat actors have all contributed. Even protective controls previously seen as bulletproof, such as MFA, have been circumvented in some successful attacks.
But it was not all doom and gloom. There was much to be optimistic about. Panelists highlighted that more cybersecurity tools and solutions are available to detect and respond to these threats, while awareness has steadily increased among their customers, with many starting to be proactive in planning for attacks.
Cybersecurity has emerged as a board-level issue due to the financial repercussions of successful breaches. But some customers are still not taking enough action to implement the recommended cybersecurity measures, though the major concern remains with smaller customers, many of which still lack basic controls.
Partners shared stories of breaches and in some cases re-breaches, where the persistence and patience of threat actors stood out. Perhaps the most worrying story was of a small Austrian company that had been informed by the country’s intelligence agency that they were on a list of a nation state’s known targets. Its objectives and the potential consequences were unknown, which contrasts with typical ransomware attacks. This made it an even greater challenge for the partner to mitigate. It also highlighted a vital point. Indicators of compromise are not always evident.
Demonstrating cyber-maturity is a competitive advantage
The common perception that cybersecurity is a cost center is changing. Demonstrating a level of cyber-maturity, with established governance in place and backed by recognized certifications, is increasingly seen as a competitive advantage. Consumers and organizations are more likely to do business with a company that has a good reputation for keeping data protected and takes cybersecurity seriously. In this case, no news (of a breach) is good news.
Increasingly, tenders for contracts are requiring bidders to have specific cybersecurity certifications, such as Cyber Essentials. It is mandatory for a lot of government contracts. Partners are fielding more requests to help their customers reach these standards, which can involve lengthy and complex processes. Likewise, customers are also requiring partners to have their own credentials and demonstrate they can respond to threats.
Incident response planning is more than a technology discussion
The key discussions in both panels focused on strengthening customers’ cybersecurity governance, in terms of defining risk, instilling accountability and establishing responsibility for key decisions. This has evolved over the last 12 months, with a greater focus on creating structured playbooks, so both customers and partners know exactly what to do when attacks happen. This must be based on an analysis of each customer to determine their risk.
Understanding their business and processes, and the criticality of their systems and data are all key elements, which require a lot of upfront work. But this is often neglected. Frameworks, such as NIST’s Identify, Protect, Detect, Respond and Recover, are useful for forming cybersecurity strategies and driving sales engagements. But a more practical approach is needed by partners in terms of providing breach assessment services and threat modelling to give customers a complete view of the risks and measures required.
Partners must start with the basics, particularly implementing best practices for backing up data. Selecting the right cybersecurity products was highlighted as an important role that partners still need to fulfill. Customers can blow their entire budget on a range of products, which may not make them more secure, as introducing too much too soon creates complexity.
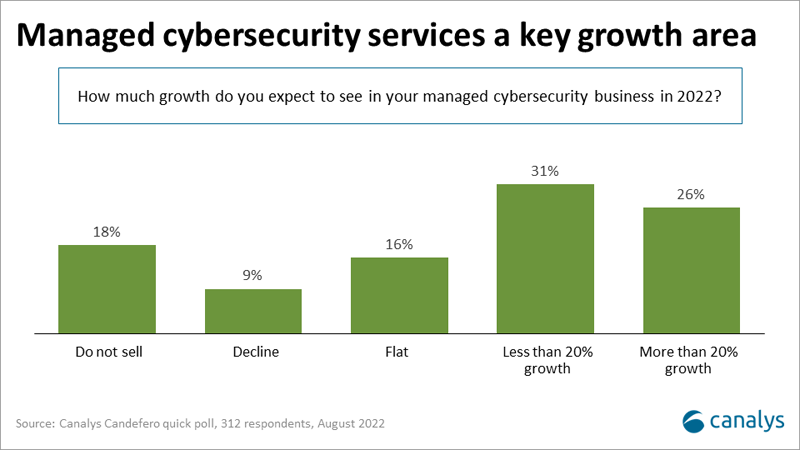
Managed cybersecurity services help reduce this complexity and accelerate customers’ cyber-resilience. This is a growth opportunity for partners, especially detection and response services. But the panelists made important points. Partners should not sell managed detection services without providing some form of response capabilities. Incident response plans are needed to rapidly contain attacks to minimize damage. But partners also need to know the limits of their capabilities and be prepared to work with response specialists to either create plans or fulfil those roles. Collaboration between partners in the cybersecurity ecosystem is essential.
Training is also a key part of cybersecurity governance, but it must be part of a company’s culture rather than treated as a checkbox to tick every six months. There are opportunities for partners to implement programs with their customers. Successful training programs are highly targeted and granular, such as focusing on specific executives or individuals with whaling and spear-phishing simulations. This must be a continuous process and not a one-off.
Cybersecurity provides long-term growth opportunities
Across both panels, there was a consensus that cybersecurity must be viewed as a long-term partnership between partners and customers. Building greater cyber-resilience is a step-by-step and continuous process. Assigning responsibility at each step is vital. Successful partners will be able to continue and expand cybersecurity conversations to drive further sales. For example, if they sold a hosted UC or contact center solution, or a specific SaaS application to a customer, then they would go back and show how they can secure them.
Share this article
CATEGORY
- All
- Canalys Forums
- Canalys Forums,Channels
- Canalys Forums,Channels,Partner Program
- Canalys Forums,Channels,Sustainability
- Canalys Forums,Sustainability
- Enterprise
- Market
- Market,Canalys Forums,Channels
- Market,Canalys Forums,Channels,Cloud
- Market,Canalys Forums,Channels,Sustainability
- Market,Channels,PC
- Market,PC
- Market,Smartphone
- Market,Technology,AR/XR/VR
- Market,Technology,Automotive
- Market,Technology,Canalys Forums,Channels
- Market,Technology,Canalys Forums,Channels,Cloud
- Market,Technology,Channels
- Market,Technology,Channels,Cloud,Partner Program
- Market,Technology,Smart Personal Audio
- Market,Technology,Smart Speaker
- Market,Technology,Smartphone
- Smart Personal Audio
- Smartphone
- Technology
- Technology,Canalys Forums,Channels,Security
- Technology,Channels
- Technology,Channels,Cloud,Partner Program
- Technology,Channels,Partner Program
- Technology,Unified Communications
- Technology,Wearable Band

